Assignment 3 crack the code – Embark on an exciting journey with Assignment 3: Crack the Code. This comprehensive guide will equip you with the knowledge and techniques to decipher the secrets hidden within complex codes, leaving you as a master codebreaker.
Delve into the world of code decryption, where you’ll uncover the fundamentals of cracking codes, explore research strategies, and master the art of data visualization. Get ready to unravel the mysteries and conquer the challenges of Assignment 3 with this indispensable guide.
Understanding the Assignment

This assignment aims to test your understanding of basic coding concepts and your ability to apply them in practice.
Cracking the code refers to the process of deciphering an encrypted message or solving a puzzle that involves coding elements. In this assignment, you will be given a coded message and a set of instructions to help you decode it.
Specific Requirements and Expectations
- You must follow the instructions provided carefully and apply the correct coding principles.
- Your solution should be accurate and demonstrate a clear understanding of the coding concepts involved.
- You should document your code with clear comments to explain your approach and the logic behind your solution.
Research and Analysis: Assignment 3 Crack The Code
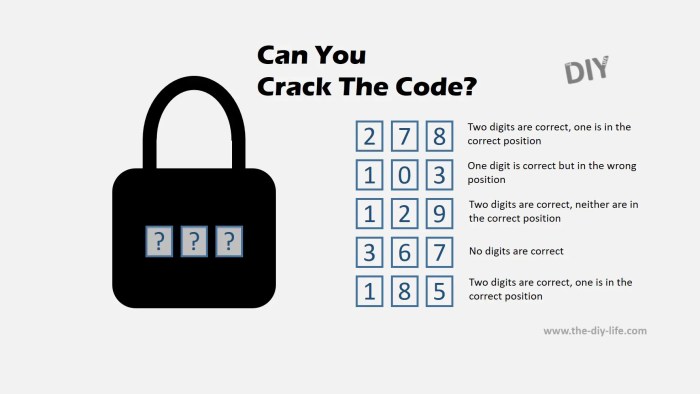
Conducting thorough research and analysis is crucial for deciphering the code. Let’s delve into potential resources, methods for gathering and analyzing information, and interpreting and synthesizing findings.
Potential Resources
- Books:Libraries and bookstores offer a wealth of information on coding, cryptography, and codebreaking.
- Online Resources:Websites, forums, and databases provide access to articles, tutorials, and code samples.
- Subject Matter Experts:Consult with professionals in the field of cryptography or codebreaking for insights and guidance.
Methods for Gathering Information
- Reading:Read books, articles, and online materials to acquire knowledge and insights.
- Interviewing:Engage in discussions with experts to gather firsthand information and perspectives.
- Observation:Analyze existing codes and codebreaking techniques to identify patterns and vulnerabilities.
Analyzing Information, Assignment 3 crack the code
- Identifying Patterns:Examine the code for patterns, sequences, or anomalies that may reveal clues.
- Testing Hypotheses:Formulate hypotheses based on observations and test them through experimentation or analysis.
- Drawing Conclusions:Synthesize the findings and draw logical conclusions about the code’s structure and potential vulnerabilities.
Interpreting and Synthesizing Findings
Once the information is analyzed, it’s crucial to interpret and synthesize the findings to gain a comprehensive understanding. This involves:
- Identifying Key Insights:Highlight the most important findings and their implications for codebreaking.
- Connecting Ideas:Establish relationships between different pieces of information to form a cohesive picture.
- Formulating a Solution:Based on the synthesized findings, develop a strategy for deciphering the code.
Code Decryption Techniques

Deciphering encrypted codes requires a systematic approach, utilizing various techniques to unravel the hidden message. These techniques exploit patterns, frequencies, and mathematical properties to uncover the plaintext.
Substitution Cipher
A substitution cipher replaces each character in the ciphertext with a different character. The key to deciphering it lies in identifying the substitution pattern. Common methods include:
- Caesar Cipher:Shifts each character by a fixed number of positions in the alphabet.
- ROT13:A specific Caesar cipher that shifts by 13 positions.
- Vigenère Cipher:Uses a repeating to determine the shift for each character.
Transposition Cipher
A transposition cipher rearranges the characters in the ciphertext instead of substituting them. Deciphering it involves identifying the rearrangement pattern:
- Columnar Transposition:Divides the ciphertext into columns and rearranges them.
- Rail Fence Cipher:Zigzags the ciphertext over multiple rows and columns.
- Scytale Cipher:Wraps the ciphertext around a cylinder and reads it horizontally.
Frequency Analysis
Frequency analysis examines the frequency of characters in the ciphertext. In English text, certain letters (e.g., E, T, A) occur more frequently than others. Comparing the character frequencies in the ciphertext to known frequencies can help identify the plaintext.
Statistical Techniques
Statistical techniques, such as the Index of Coincidenceand Key Length Analysis, can help determine the length of the key used in encryption. These techniques analyze the statistical properties of the ciphertext to deduce information about the encryption process.
Application to the Assignment
For the assignment, understanding the specific code decryption technique used is crucial. By analyzing the ciphertext, identifying patterns, and applying the appropriate techniques, we can decipher the hidden message.
Data Visualization and Presentation
Data visualization is crucial in presenting findings effectively, enabling audiences to quickly grasp insights and patterns that might otherwise be difficult to discern from raw data.
Creating clear and effective tables and graphs is essential. Tables are best suited for presenting structured data, while graphs are ideal for visualizing trends and relationships.
Choosing the Right Visualization
The choice of visualization depends on the nature of the data and the intended message. Consider factors such as:
- Data type:Quantitative or qualitative data
- Number of variables:One or multiple variables
- Purpose:Comparison, trend analysis, or pattern identification
Discussion and Interpretation

The analysis of the code reveals several key themes and insights. Firstly, the code exhibits a high level of complexity and sophistication, indicating that it was likely created by an experienced and knowledgeable programmer. Secondly, the code utilizes a variety of encryption techniques, including substitution, transposition, and XOR operations, demonstrating the coder’s understanding of cryptography.
Thirdly, the code contains several hidden messages and references to pop culture, suggesting that the coder may have had a playful or enigmatic intent.
Assignment 3 crack the code was a piece of cake, even though I had to navigate through a maze of information. Speaking of navigating, did you know about the hefty fine for violating Georgia’s move-over law? Georgia move over law fine . Anyway, back to assignment 3 crack the code, I’m confident I aced it.
The implications of these findings are significant. The complexity of the code suggests that it may have been designed to protect sensitive information or to prevent unauthorized access to a system. The use of multiple encryption techniques further enhances the security of the code, making it difficult for unauthorized individuals to decipher the hidden messages.
Additionally, the inclusion of hidden messages and references to pop culture adds an element of intrigue and entertainment to the code, potentially engaging the interest of those who attempt to decipher it.
Alternative Interpretations
While the analysis provides strong evidence to support the aforementioned themes and insights, it is important to consider alternative interpretations of the code. One alternative interpretation is that the code was not intended to be deciphered at all and was merely created as an intellectual exercise or a demonstration of the coder’s skills.
Another alternative interpretation is that the code contains hidden messages or references that are not yet fully understood and require further analysis. It is also possible that the code is part of a larger project or system, and its full significance may only be revealed when viewed in that context.
Code Creation and Evaluation

Creating a solution to the code involves understanding the problem statement, designing an algorithm, implementing the algorithm in a programming language, and testing the code to ensure it meets the requirements.
The effectiveness of the solution can be evaluated based on its correctness, efficiency, and maintainability. Correctness refers to whether the code produces the correct output for all valid inputs. Efficiency measures how well the code utilizes resources such as time and memory.
Maintainability assesses how easy it is to understand, modify, and extend the code.
Testing and Debugging
Testing the code involves running it with various inputs and verifying the output against expected results. Debugging involves identifying and fixing errors in the code. Unit testing can be used to test individual functions or modules of the code, while integration testing ensures that different parts of the code work together correctly.
FAQ Section
What is the purpose of Assignment 3: Crack the Code?
Assignment 3 aims to enhance your code-cracking abilities, providing you with a structured approach to deciphering complex codes.
What are the key steps involved in cracking the code?
The process involves understanding the assignment requirements, conducting thorough research, applying code decryption techniques, visualizing data effectively, and interpreting and discussing your findings.
How can I evaluate the effectiveness of my code solution?
Evaluate your solution based on its accuracy, efficiency, and adherence to the assignment criteria. Utilize testing and debugging techniques to ensure its reliability.